PagerDuty - SSO Configuration

This application has not been formally tested by Kelvin Zero Inc. It is provided solely as a reference guide. If you encounter any issues, kindly submit a ticket directly through the support desk.

This documentation provides a step-by-step guide to setting up Single Sign-On (SSO) for PagerDuty using Multi-Pass. SSO simplifies authentication by allowing access to multiple applications with a single set of credentials, improving both security and user experience.

To set up Multi-Pass with PagerDuty, ensure you meet the following requirements:
- PagerDuty admin rights
- MPAS Admin rights
- Make sure that all users intended to use SSO in PagerDuty are registered in your IdP and have the necessary permissions to access PagerDuty.
Important: Custom elements in URLs (like realm names) are case sensitive. Make sure to match the exact casing from your environment.
PagerDuty - SSO configuration
Step 1 - Obtain Tenant Certificate from Multi-Pass (IdP)
- Open Multi-Pass Dashboard
- Select the correct tenant and go to Integrations > Applications
- Select SAML in the custom integration section
- Under Tenant Certificate, switch the left box to Text and select Copy Contents
- Paste the certificate into a Notepad file for later use
Step 2 - Configure PagerDuty as the Service Provider (SP)
- Log into PagerDuty as an Administrator
- Navigate to User Icon > Account Settings > Single Sign-On
- Select the SAML option
- Paste the Certificate from Step 1 into the X.509 Certificate field
- Set the Login URL to:
https://ca.auth.kzero.com/realms/<TENANT_NAME>/protocol/saml - Set the Logout URL to:
https://ca.auth.kzero.com/realms/<TENANT_NAME>/protocol/saml - Check: Require EXACT authentication context comparison
- Uncheck: Allow username/password login
- Click Save
Step 3 - Configure Multi-Pass as the Identity Provider (IdP)
- In Multi-Pass, return to Integrations > Applications > Custom SAML App
- Confirm and complete the following fields:
| Field | Value |
|---|---|
| Client ID (=SP Entity ID) | https://<SUBDOMAIN>.pagerduty.com |
| Name | pagerduty |
| Description | PagerDuty SSO integration |
| Assertion Consumer Service URL | https://<SUBDOMAIN>.pagerduty.com/sso/saml/consume |
| NameID Policy Format | email |
- Go to the Advanced Console by clicking on the right side of your screen
- Click on Client and use the search bar to look for Pagerduty
- Make sure all the fields are populated
General settings (Multi-Pass)
| Field | Value |
|---|---|
| Client ID | https://<SUBDOMAIN>.pagerduty.com |
| Name | pagerduty |
| Description | PagerDuty SSO Integration |
| Always display in UI | ON |
Access settings (Multi-Pass)
| Field | Value |
|---|---|
| Home URL (IdP-initiated) | https://ca.auth.kzero.com/realms/<TENANT_NAME>/protocol/saml/clients/<APP_NAME> |
| Valid Redirect URIs (ACS) | https://<SUBDOMAIN>.pagerduty.com/sso/saml/consume |
| IDP-Initiated SSO URL Name | <APP_NAME> |
SAML Capabilities
| Setting | Value |
|---|---|
| Name ID Format | email |
| Force Name ID Format | ON |
| Force POST Binding | ON |
| Include AuthnStatement | ON |
Signature & Encryption
| Setting | Value |
|---|---|
| Sign Documents | OFF |
| Sign Assertions | ON |
- Navigate to the Keys tab and ensure both parameters are set to
OFF
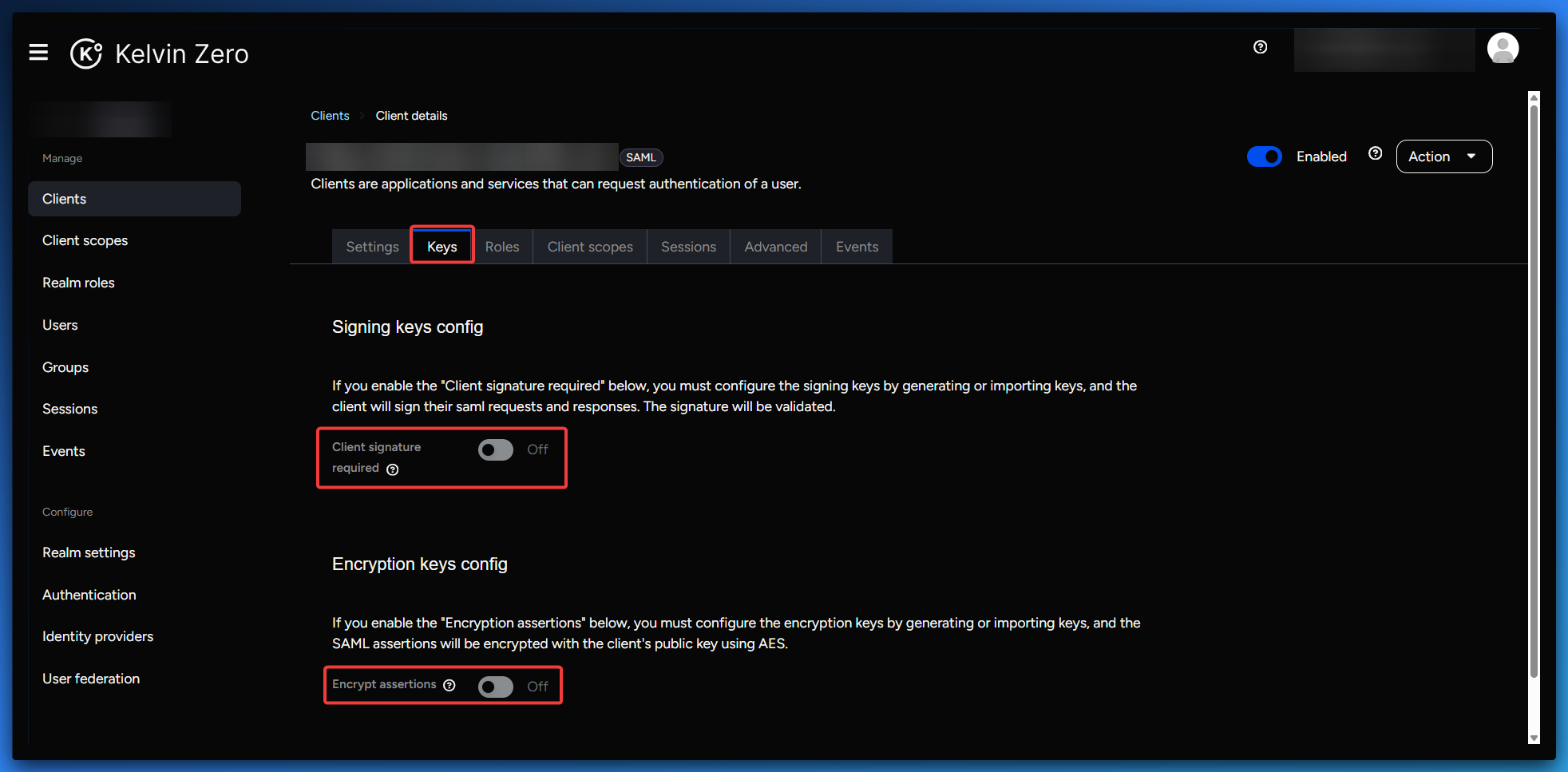
- In the Advanced tab, set Assertion Consumer Service POST Binding URL to the same value as Valid Redirect URIs (ACS)
Related Articles
D2L Brightspace - SSO Integration
This application has not been formally tested by Kelvin Zero Inc. It is provided solely as a reference guide. If you encounter any issues, kindly submit a ticket directly through the support desk. This documentation provides a step-by-step guide to ...Mulesoft - SSO Integration
This application has been formally tested by Kelvin Zero Inc. This documentation provides a step-by-step guide to setting up Single Sign-On (SSO) for Mulesoft using Multi-Pass. SSO simplifies user authentication by allowing access to multiple ...SAML SSO Integration Guide
This guide provides an overview of how to configure SAML Single Sign-On (SSO) between Multi-Pass and a third-party Service Provider (SP). Multi-Pass acts as the Identity Provider (IdP) in this federation model. Multi-Pass is working on SCIM support ...Miro - SSO configuration
This documentation has been tested and approved by Kelvin Zero's team This documentation provides a step-by-step guide to setting up Single Sign-On (SSO) for Miro using MPAS. SSO simplifies user authentication by allowing access to multiple ...Pipedrive – SSO configuration
This application has been formally tested by Kelvin Zero Inc. This documentation provides a step-by-step guide to setting up Single Sign-On (SSO) for Pipedrive using Multi-Pass. SSO simplifies user authentication by allowing access to multiple ...